The cmplid:// security management solution provides ongoing passive compliance and vulnerability monitoring far exceeding simplistic GRC metric tracking.
cmplid:// enables consistent cyber security management and is a leading solution within the nuclear power industry.
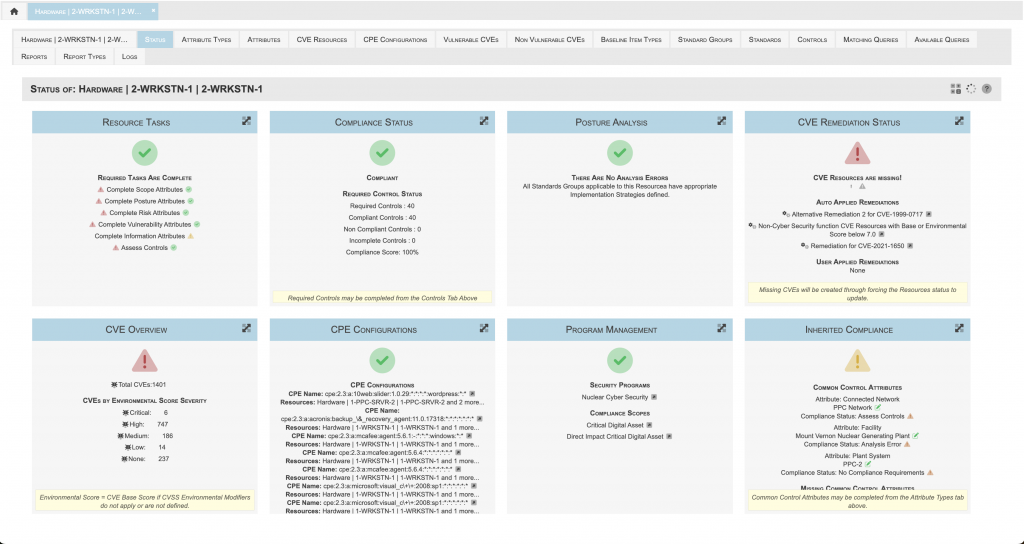
cmplid:// integrates security program management with everyday operations to provide:
- A consistent understanding of enterprise security programs
- A mechanism for communicating responsibilities
- Clear documentation of the implementation and ongoing management of the programs

Resource Based
The cmplid:// solution utilizes the concept of control inheritance, granularly applied to the assets requiring protection for any security program. This ensures the implementation and maintenance of appropriate and functional security programs.
Characteristic Aligned
Characteristics of resources or other defined objects determine the scope of managed security program(s). In addition, characteristics of objects indicate the following:
- For which resources the security standards must be addressed
- How the security standards will be implemented on specific resources
- Any compensating controls applied that alleviate application of otherwise required controls
- Controls that reduce (through application of Environmental Scores) the severity of CVEs for specific resources
- Vulnerability remediation actions that must be taken to mitigate identified CVEs
Risk Informed
Reports provide detailed analysis of the purpose and consequence of the individual security standards, attack pathways, and the threat agents that may potentially exploit vulnerabilities in the resources within scope.
Compliance Management
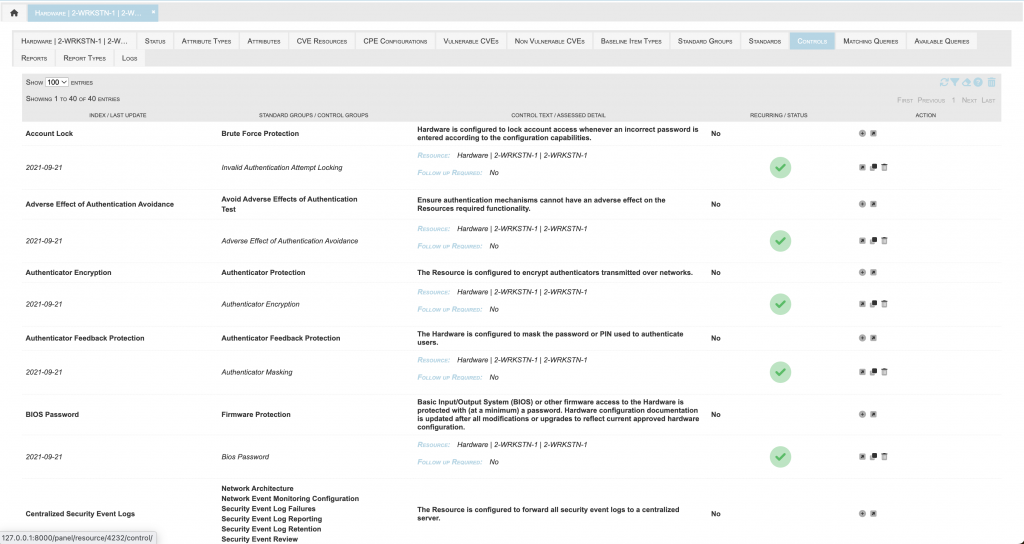
Documents detailed implementation guidelines for all security requirements within managed security programs by performing the following analysis:
- Associating each requirement (Standard) to the applicable type(s) of resources
- Associating Standards with user-defined Compliance Scopes, or categories of Resources, to which the Standards are intended to protect.
- Grouping Standards based on the characteristics of the Resources.
- Defining Controls and indicating all of the various methods to implement those Standards. Implementation may be defined as one of the following:
- Direct: Implements the Standard as defined in the source document
- Alternate: Implements a compensatory control (used when Direct implementation is infeasible)
- Inherited: A control implemented on a distinct Resource provides the requisite capability for the Resource in question
The analysis is clearly documented, consistent, collaborative, and facilitated by an extremely powerful and flexible query mechanism.
cmplid:// supports any and all security standards including internal, third-party and government regulations.
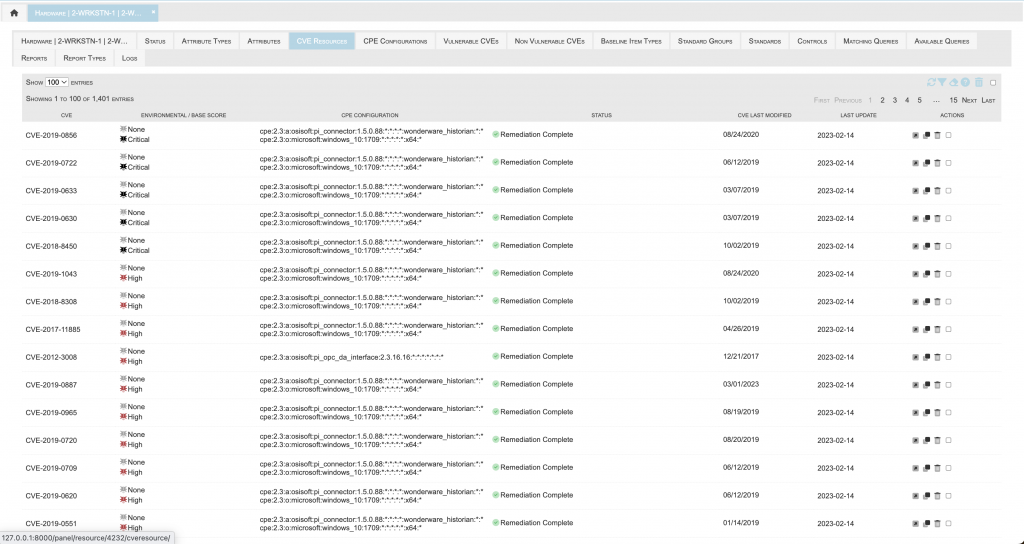
Vulnerability Management
The cmplid:// database contains the entirety of the National Vulnerability Database of Common Vulnerability and Exposures (CVE) hosted by NIST. This data is updated consistent with the NVD update schedule.
Additionally, all Common Platform Enumerations (CPE) used by the NVD to associate CVEs to affected applications, operating systems, and hardware are maintained as well.
CPE Configurations within cmplid://, containing one or more CPEs and one or more Resources, are used to identify vulnerable software throughout the end-user’s organization. Whenever CPE Configurations are defined or modified, as well as when other relevant changes occur, cmplid:// will create a record for each Resource vulnerable to a CVE.
Environmental Modifiers can be defined to facilitate the automatic calculation of CVSS Environmental Scores specific to Resources vulnerable to CVEs.
Remediation actions may be defined that indicate what, if any, automated or manual actions must be taken to mitigate CVEs.
The analysis is clearly documented, consistent, collaborative, and facilitated by the query framework.